What is Pass4itsure Cisco 210-060 dumps exam training materials? The Implementing Cisco Collaboration Devices v1.0 (210-060 CICD) exam is a 75 Minutes (55 – 65 questions) assessment in pass4itsure that is associated with the CCNA Collaboration certification. “Implementing Cisco Collaboration Devices v1.0” is the exam name of Pass4itsure Cisco 210-060 dumps test which designed to help candidates prepare for and pass the Cisco 210-060 exam.
Discount Cisco 210-060 dumps CICD pdf CCNA Collaboration certification are based on the real exam video training. Pass4itsure will provide all the latest and accurate exam practice questions and answers for the staff to participate in https://www.pass4itsure.com/210-060.html dumps practice questions.
[New Pass4itsure 210-060 Dumps Version From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWNmlXYjFDT0t3UWc
[New Pass4itsure 640-911 Dumps Version From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWSDRkZ3Rob1lLcDg
Latest and Most Accurate Pass4itsure 210-060 Dumps Exam Q&As:
QUESTION 10
A user would like all calls to be forwarded to voice mail. The user’s phone is not set up with a soft key for this feature. Which option accomplishes this configuration from within the Cisco Unified Communication Administrator Directory Number configuration page?
A. Call Forward and Pickup Settings > Forward No Coverage External > Select voice mail check box
B. Call Forward and Pickup Settings > Forward Busy External > Select voice mail check box
C. Call Forward and Pickup Settings > Forward All > Select voice mail check box
D. Call Forward and Pickup Settings > Forward Unregistered External > Select voice mail check box
210-060 exam Correct Answer: C
QUESTION 11
A new user has successfully registered Cisco Jabber. Which option verifies that the Jabber client is connected to all appropriate back-end systems?
A. Show Connection Status
B. Report A Problem
C. Advanced Settings
D. About Jabber
E. Reset Jabber
Correct Answer: A
QUESTION 12
Which two technologies comprise a Cisco Presence deployment? (Choose two.)
A. Cisco Unified Presence Server
B. Cisco Unity Connection
C. Cisco Unified Communications Manager
D. Active Directory
E. Cisco Unified Border Element
F. Cisco Expressway
210-060 dumps Correct Answer: AC
QUESTION 13
Which three network elements are crucial when deploying VoIP devices? (Choose three.)
A. Round-trip time
B. QoS markings
C. Bandwidth
D. Ethernet
E. Fibre
F. Token ring
Correct Answer: ABC
QUESTION 14
Use the router console to view the configuration and answer the question.
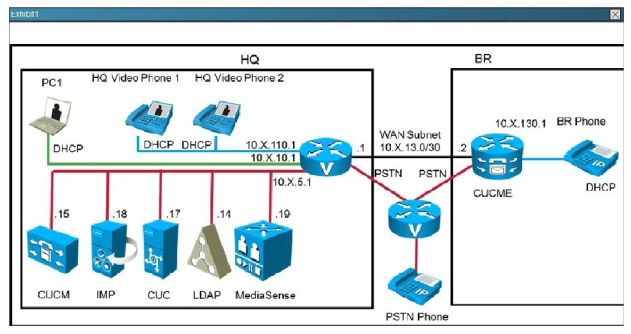

When a call is placed from the Branch Router phone to the PSTN number of 914085551212, the call is failing. What dial-peer is supposed to be used and why is the call failing? Select 2 (two)
A. dial-peer voice 910 pots
B. dial-peer voice 9 pots
C. dial-peer voice 9001 voip
D. destination pattern is incorrect
E. prefix is missing from the dial-peer
F. the port assignment is incorrect in the dial-peer
G. the port number is missing in the dial-peer
210-060 pdf Correct Answer: BF
QUESTION 15
Which of the following proxy servers is also referred to as transparent proxies or forced proxies?
A. Intercepting proxy server
B. Anonymous proxy server
C. Reverse proxy server
D. Tunneling proxy server
Correct Answer: A
QUESTION 16
Which of the following security policies will you implement to keep safe your data when you connect your Laptop to the office network over IEEE 802.11 WLANs? Each correct answer represents a complete solution. Choose two.
A. Using a protocol analyzer on your Laptop to monitor for risks.
B. Using an IPSec enabled VPN for remote connectivity.
C. Using portscanner like nmap in your network.
D. Using personal firewall software on your Laptop.
210-060 vce Correct Answer: BD
QUESTION 17
Which of the following is the first computer virus that was used to infect the boot sector of storage media
formatted with the DOS File Allocation Table (FAT) file system?
A. I love you
B. Melissa
C. Tequila
D. Brain
Correct Answer: D
QUESTION 18
Which of the following needs to be documented to preserve evidences for presentation in court?
A. Incident response policy
B. Account lockout policy
C. Separation of duties
D. Chain of custody
210-060 exam Correct Answer: D
QUESTION 19
Kerberos is a computer network authentication protocol that allows individuals communicating over a non secure network to prove their identity to one another in a secure manner. Which of the following statements are true about the Kerberos authentication scheme? Each correct answer represents a complete solution. Choose all that apply.
A. Kerberos requires continuous availability of a central server.
B. Kerberos builds on Asymmetric key cryptography and requires a trusted third party.
C. Dictionary and brute force attacks on the initial TGS response to a client may reveal the subject’spasswords.
D. Kerberos requires the clocks of the involved hosts to be synchronized.
Correct Answer: ACD
QUESTION 20
Which of the following is used in asymmetric encryption?
A. Public key and user key
B. SSL
C. Public key and private key
D. NTFS
210-060 dumps Correct Answer: C
QUESTION 21
Sam, a malicious hacker, targets the electric power grid of Umbrella Inc. and gains access to the electronic control systems. Which of the following types of cybercrime has Sam performed?
A. Cyber defamation
B. Cybertrespass
C. Cyberterrorism
D. Cybertheft
Correct Answer: C
QUESTION 22
Maria works as a Desktop Technician for PassGuide Inc. She has received an e-mail from the MN
Compensation Office with the following message:
Dear Sir/Madam,
My name is Edgar Rena, the director of compensation here at the MN Compensation Office in Chicago.
We receive so many complaints about fraudulent activities that have been taking place in your region for
the past few years. Due to the high volume loss of money, the MN compensation department has had an
agreement with the appropriate authority to compensate each victim with a sum of USD$500,000.00.
You were selected among the list of people to be paid this sum. To avoid any imperative mood by intending scammers, your payment has been transmuted into an International bank draft which can be
cashed at any local bank in your country. Please fill the below details and send it to our secretary for your compensation bank draft. Further instructions shall be given to you by our secretary as soon as you contact him. To avoid losing your compensation, you are requested to pay the sum of $350 for Insurance Premium to our secretary. Thanks and God bless. If Maria replies to this mail, which of the following attacks may she become vulnerable to?
A. Phishing attack
B. SYN attack
C. CookieMonster attack
D. Mail bombing
210-060 pdf Correct Answer: A
QUESTION 23
Victor works as a network administrator for DataSecu Inc. He uses a dual firewall Demilitarized Zone (DMZ) to insulate the rest of the network from the portions that is available to the Internet. Which of the following security threats may occur if DMZ protocol attacks are performed? Each correct answer represents a complete solution. Choose all that apply.
A. The attacker can exploit any protocol used to go into the internal network or intranet of thecompany.
B. The attacker can gain access to the Web server in a DMZ and exploit the database.
C. The attacker can perform a Zero Day attack by delivering a malicious payload that is not a part of the intrusion detection/prevention systems guarding the network.
D. The attacker managing to break the first firewall defense can access the internal network without breaking the second firewall if it is different.
Correct Answer: ABC
QUESTION 24
Which of the following Linux rootkits is installed via stolen SSH keys?
A. Phalanx2
B. Beastkit
C. Adore
D. Linux.Ramen
210-060 vce Correct Answer: A
QUESTION 25
Which of the following is a set of exclusive rights granted by a state to an inventor or his assignee for a fixed period of time in exchange for the disclosure of an invention?
A. Snooping
B. Copyright
C. Utility model
D. Patent
Correct Answer: D
QUESTION 26
Jason works as a System Administrator for Passguide Inc. The company has a Windows-based network.
Sam, an employee of the company, accidentally changes some of the applications and system settings. He complains to Jason that his system is not working properly. To troubleshoot the problem, Jason diagnoses the internals of his computer and observes that some changes have been made in Sam’s computer registry. To rectify the issue, Jason has to restore the registry. Which of the following utilities can Jason use to accomplish the task? Each correct answer represents a complete solution. Choose all that apply.
A. Reg.exe
B. Resplendent registrar
C. EventCombMT
D. Regedit.exe
210-060 exam Correct Answer: ABD
QUESTION 27
Victor works as a professional Ethical Hacker for SecureEnet Inc. He has been assigned a job to test an image, in which some secret information is hidden, using Steganography. Victor performs the following techniques to accomplish the task:
1. Smoothening and decreasing contrast by averaging the pixels of the area where significant color transitions occurs.
2. Reducing noise by adjusting color and averaging pixel value.
3. Sharpening, Rotating, Resampling, and Softening the image.
Which of the following Steganography attacks is Victor using?
A. Steg-Only Attack
B. Chosen-Stego Attack
C. Active Attacks
D. Stegdetect Attack
Correct Answer: C
QUESTION 28
What is the major difference between a worm and a Trojan horse?
A. A worm is self replicating, while a Trojan horse is not.
B. A worm is a form of malicious program, while a Trojan horse is a utility.
C. A worm spreads via e-mail, while a Trojan horse does not.
D. A Trojan horse is a malicious program, while a worm is an anti-virus software.
210-060 dumps Correct Answer: A
QUESTION 29
John works as a Network Security Administrator for NetPerfect Inc. The manager of the company has told John that the company’s phone bill has increased drastically. John suspects that the company’s phone system has been cracked by a malicious hacker. Which attack is used by malicious hackers to crack the phone system?
A. Sequence++ attack
B. Phreaking
C. Man-in-the-middle attack
D. War dialing
Correct Answer: B
QUESTION 30
You work as a professional Computer Hacking Forensic Investigator for DataEnet Inc. You want to investigate e-mail information of an employee of the company. The suspected employee is using an online e-mail system such as Hotmail or Yahoo. Which of the following folders on the local computer will you review to accomplish the task? Each correct answer represents a complete solution. Choose all that apply.
A. Download folder
B. History folder
C. Temporary Internet Folder
D. Cookies folder
210-060 pdf Correct Answer: BCD
QUESTION 31
John works as a Network Security Professional. He is assigned a project to test the security. He is working on the Linux operating system and wants to install an Intrusion Detection System on the We-are-secure server so that he can receive alerts about any hacking attempts.Which of the following tools can John use to accomplish the task? Each correct answer represents a complete solution. Choose all that apply.
A. Samhain
B. Tripwire
C. Snort
D. SARA
Correct Answer: AC

Pass4itsure is a professional website to specially provide training tools for IT certification exams and a good choice to help you pass Cisco 210-060 dumps practice questions,too. Pass4itsure provide exam materials about https://www.pass4itsure.com/210-060.html dumps practice questions for you to consolidate learning opportunities.