
The latest 312-50V12 Dumps contains 1703 exam questions and answers, which are edited, reviewed, modified, and verified by the EC-Council 312-50V12 professional team. The guaranteed coverage rate exceeds 90%, which is the real best exam solution.
Lead4Pass updates EC-Council CEH v12 Exam Solutions throughout the year! Make sure the 312-50V12 dumps you download are up-to-date every time!
more importantly! Download EC-Council 312-50V12 Dumps: https://www.pass4itsure.com/312-50v12.html Enjoy 365 days of free updates!
Moreover, Lead4Pass 312-50V12 dumps provide PDF and VCE two learning formats, which you can choose according to your usage habits! Help you learn easily and pass the EC-Council CEH v12 certification exam easily.
Sharing some of the latest 312-50V12 Dumps exam questions:
| From | Number of exam questions | Type |
| Pass4itsure | 15 | Exam questions and answers |
Question 1:
Let \’s imagined three companies (A, B, and C), all competing in a challenging global environment. Companies A and B are working together in developing a product that will generate a major competitive advantage for them.
Company A has a secure DNS server while company B has a DNS server vulnerable to spoofing. With a spoofing attack on the DNS server of company B, company C gains access to outgoing e-mails from company B.
How do you prevent DNS spoofing?
A. Install DNS logger and track vulnerable packets
B. Disable DNS timeouts
C. Install DNS Anti-spoofing
D. Disable DNS Zone Transfer
Correct Answer: C
Question 2:
Password cracking programs reverse the hashing process to recover passwords.(True/False.)
A. True
B. False
Correct Answer: B
Question 3:
What is not a PCI compliance recommendation?
A. Use a firewall between the public network and the payment card data.
B. Use encryption to protect all transmission of cardholder data over any public network.
C. Rotate employees handling credit card transactions on a yearly basis to different departments.
D. Limit access to cardholder data to as few individuals as possible.
Correct Answer: C
https://www.pcisecuritystandards.org/pci_security/maintaining_payment_security Build and Maintain a Secure Network
1.
Install and maintain a firewall configuration to protect cardholder data.
2.
Do not use vendor-supplied defaults for system passwords and other security parameters. Protect Cardholder Data
3.
Protect stored cardholder data.
4.
Encrypt transmission of cardholder data across open, public networks. Maintain a Vulnerability Management Program
5.
Use and regularly update anti-virus software or programs.
6.
Develop and maintain secure systems and applications. Implement Strong Access Control Measures
7.
Restrict access to cardholder data by business need-to-know.
8.
Assign a unique ID to each person with computer access.
9.
Restrict physical access to cardholder data. Regularly Monitor and Test Networks
10.
Track and monitor all access to network resources and cardholder data.
11.
Regularly test security systems and processes. Maintain an Information Security Policy
12.
Maintain a policy that addresses information security for employees and contractors.
Question 4:
PGP, SSL, and IKE are all examples of which type of cryptography?
A. Digest
B. Secret Key
C. Public Key
D. Hash Algorithm
Correct Answer: C
Question 5:
What does a firewall check to prevent particular ports and applications from getting packets into an organization?
A. Transport layer port numbers and application layer headers
B. Presentation layer headers and the session layer port numbers
C. Network layer headers and the session layer port numbers
D. Application layer port numbers and the transport layer headers
Correct Answer: A
Question 6:
Boney, a professional hacker, targets an organization for financial benefits. He performs an attack by sending his session ID using a MITM attack technique. Boney first obtains a valid session ID by logging into a service and later feeds the same session 10 to the target employee.
The session ID links the target employee to the Boney account page without disclosing any information to the victim. When the target employee clicks on the link, all the sensitive payment details entered in a form are linked to Boney’s account.
What is the attack performed by Boney in the above scenario?
A. Session donation attack
B. Session fixation attack
C. Forbidden attack
D. CRIME attack
Correct Answer: A
In a session donation attack, the attacker donates their own session ID to the target user. In this attack, the attacker first obtains a valid session ID by logging into a service and later feeds the same session ID to the target user.
This session ID links a target user to the attacker\’s account page without disclosing any information to the victim. When the target user clicks on the link and enters the details (username, password, payment details, etc.) in a form, the entered details are linked to the attacker\’s account.
To initiate this attack, the attacker can send their session ID using techniques such as cross-site cooking, a MITM attack, and session fixation. A session donation attack involves the following steps.
Question 7:
Ben purchased a new smartphone and received some updates on it through the OTA method. He received two messages: one with a PIN from the network operator and another asking him to enter the PIN received from the operator.
As soon as he entered the PIN, the smartphone started functioning in an abnormal manner. What is the type of attack performed on Ben in the above scenario?
A. Advanced SMS phishing
B. Bypass SSL pinning
C. Phishing
D. Tap \’n ghost attack
Correct Answer: A
Question 8:
By using a smart card and pin, you are using a two-factor authentication that satisfies
A. Something you are and something you remember
B. Something you have and something you know
C. Something you know and something you are
D. Something you have and something you are
Correct Answer: B
Two-factor Authentication or 2FA is a user identity verification method, where two of the three possible authentication factors are combined to grant access to a website or application.
1) something the user knows,
2) something the user has, or
3) something the user is.
The possible factors of authentication are:
Something the User Knows:
This is often a password, passphrase, PIN, or secret question. To satisfy this authentication challenge, the user must provide information that matches the answers previously provided to the organization by that user, such as “Name the town
in which you were born.”
Something the User Has:
This involves entering a one-time password generated by a hardware authenticator. Users carry around an authentication device that will generate a one-time password on command. Users then authenticate by providing this code to the
organization. Today, many organizations offer software authenticators that can be installed on the user\’s mobile device.
Something the User Is:
This third authentication factor requires the user to authenticate using biometric data. This can include fingerprint scans, facial scans, behavioral biometrics, and more. For example: In internet security, the most used factors of authentication
are:
something the user has (e.g., a bank card) and something the user knows (e.g., a PIN code). This is two-factor authentication. Two-factor authentication is also sometimes referred to as strong authentication, Two-Step Verification, or 2FA.
The key difference between Multi-Factor Authentication (MFA) and Two-Factor Authentication (2FA) is that, as the term implies, Two-Factor Authentication utilizes a combination of two out of three possible authentication factors. In contrast,
Multi-Factor Authentication could utilize two or more of these authentication factors.
Question 9:
Which system consists of a publicly available set of databases that contain domain name registration contact information?
A. WHOIS
B. CAPTCHA
C. IANA
D. IETF
Correct Answer: A
Question 10:
Gilbert, a web developer, uses a centralized web API to reduce complexity and increase the Integrity of updating and changing data. For this purpose, he uses a web service that uses HTTP methods such as PUT. POST. GET. and DELETE can improve the overall performance, visibility, scalability, reliability, and portability of an application.
What is the type of web-service API mentioned in the above scenario?
A. JSON-RPC
B. SOAP API
C. RESTful API
D. REST API
Correct Answer: C
*REST is not a specification, tool, or framework, but instead is an architectural style for web services that serve as a communication medium between various systems on the web.
*RESTful APIs, which are also known as RESTful services, are designed using REST principles and HTTP communication protocols RESTful is a collection of resources that use HTTP methods such as PUT, POST, GET, and DELETE
RESTful API: RESTful API is a RESTful service that is designed using REST principles and HTTP communication protocols. RESTful is a collection of resources that use HTTP methods such as PUT, POST, GET, and DELETE.
RESTful API is also designed to make applications independent to improve the overall performance, visibility, scalability, reliability, and portability of an application.
APIs with the following features can be referred to as RESTful APIs: o Stateless: The client end stores the state of the session; the server is restricted to save data during the request processing o Cacheable: The client should save responses (representations) in the cache. This feature can enhance API performance pg. 1920 CEHv11 manual.
https://cloud.google.com/files/apigee/apigee-web-api-design-the-missing-link-ebook.pdf
The HTTP methods GET, POST, PUT or PATCH, and DELETE can be used with these templates to read, create, update, and delete description resources for dogs and their owners.
This API style has become popular for many reasons. It is straightforward and intuitive, and learning this pattern is similar to learning a programming language API.
APIs like this one are commonly called RESTful APIs, although they do not display all of the characteristics that define REST (more on REST later).
Question 11:
An attacker runs a Netcat tool to transfer a secret file between two hosts.
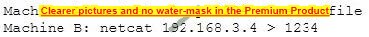
He is worried about information being sniffed on the network.
How would the attacker use Netcat to encrypt the information before transmitting it onto the wire?
A. Machine A: netcat -l -p -s password 1234 < testfileMachine B: netcat
B. Machine A: netcat -l -e magic key -p 1234 < testfileMachine B: netcat
C. Machine A: netcat -l -p 1234 < test file -pw passwordMachine B: netcat 1234 -pw password
D. Use crypt cat instead of netcat
Correct Answer: D
Question 12:
Every company needs a formal written document that spells out to employees precisely what they are allowed to use the company\’s systems for, what is prohibited, and what will happen to them if they break the rules.
Two printed copies of the policy should be given to every employee as soon as possible after they join the organization. The employee should be asked to sign one copy, which should be safely filed by the company.
No one should be allowed to use the company\’s computer systems until they have signed the policy in acceptance of its terms.
What is this document called?
A. Information Audit Policy (IAP)
B. Information Security Policy (ISP)
C. Penetration Testing Policy (PTP)
D. Company Compliance Policy (CCP)
Correct Answer: B
Question 13:
What would you enter if you wanted to perform a stealth scan using Nmap?
A. nmap -sM
B. nmap -sU
C. nmap -sS
D. nmap -sT
Correct Answer: C
Question 14:
Henry is a penetration tester who works for XYZ organization. While performing enumeration on a client organization, he queries the DNS server for a specific cached DNS record.
Further, by using this cached record, he determines the sites recently visited by the organization\’s user. What is the enumeration technique used by Henry in the organization?
A. DNS zone walking
B. DNS cache snooping
C. DNS SEC zone walking
D. DNS cache poisoning
Correct Answer: B
Question 15:
Which of the following Linux commands will resolve a domain name into IP address?
A. >host-t a hackeddomain.com
B. >host-t ns hackeddomain.com
C. >host -t soa hackeddomain.com
D. >host -t AXFR hackeddomain.com
Correct Answer: A
…
Practice the latest 312-50V12 Dumps exam questions online to help you learn more about the latest EC-Council CEH v12 certification exam! Improve professional skills!
Use EC-Council CEH v12 Exam Solutions: Download Latest 312-50V12 dumps: https://www.pass4itsure.com/312-50v12.html (PDF+VCE), to help you pass the exam 100% successfully.