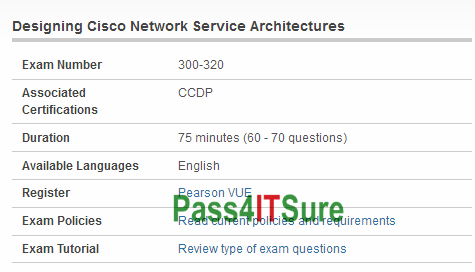
How many question and what is passing score for Cisco 300-320 dumps? The Designing Cisco Network Service Architectures (300-320 ARCH) exam is a 75 minutes (60 – 70 questions) assessment in pass4itsure that is associated with the CCDP certification. The need for best Cisco CCDP 300-320 dumps exam video study actual test Designing Cisco Network Service Architectures. “Designing Cisco Network Service Architectures” is the exam name of Pass4itsure Cisco 300-320 dumps test which designed to help candidates prepare for and pass the Cisco 300-320 exam. For this Cisco Designing Cisco Network Service Architectures exam upgrading the qualification and skills are necessary. Even Cisco certified professionals require upgrading themselves. Now the https://www.pass4itsure.com/300-320.html dumps new questions arises how to go through Cisco 300-320 certification. The answer is so simple do preparation for Designing Cisco Network Service Architectures exam.
[New Pass4itsure 300-320 Dumps Version From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWck1GZWpsWHY4ZU0
[New Pass4itsure 300-360 Dumps Version From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWRzV4WUQyeVN2N2c
Latest and Most Accurate Pass4itsure 300-320 Dumps Exam Q&As:
QUESTION 75
What Nexus technology avoids blocking links between the access layer and the aggregation layer in a data center network design?
A. FCoE
B. LACP
C. vPC
D. FEX
300-320 exam Correct Answer: C
QUESTION 76
Which option is an advanced WAN services design consideration for a multipoint architecture that connects two or more customer devices using Ethernet bridging techniques over an MPLS network?
A. VPLS
B. Metro Ethernet
C. MPLS
D. SONET/SDH
Correct Answer: A
QUESTION 77
Which protocol is used in an in-band network and why?
A. UDP, because it is connectionless
B. SSH, because the username and password are encrypted
C. Telnet, because the username and password are sent in clear
D. MSDP, because it uses TCP as its transport protocol
300-320 dumps Correct Answer: B
QUESTION 78
A company implemented VoIP in a campus network and now wants a consistent method to implement using AutoQoS. Which two parameters must be considered before AutoQoS is configured? (Choose two.)
A. CEF must be enabled.
B. AutoQoS is available only on routers.
C. Traffic discovery must be performed manually.
D. No service policy can be applied already.
E. Manual traffic analysis must be performed.
Correct Answer: AD
QUESTION 79
Which two benefits are achieved if a network is designed properly with a structured addressing scheme? (Choose two.)
A. efficient ACLs
B. improved redundancy
C. hardened security
D. easier troubleshooting
E. added resiliency
300-320 pdf Correct Answer: AD
QUESTION 80
Which of the following features might be used by the Enterprise Campus network designer as a means of route filtering?
A. IPv4 static routes
B. Route tagging using a route map in an ACL
C. Tagging routes using the BGP MED
D. EIGRP stub networks
Correct Answer: D
QUESTION 81
An outcome of effective security governance is:
A. business dependency assessment
B. strategic alignment.
C. risk assessment.
D. planning.
300-320 vce Correct Answer: B
Explanation
Explanation/Reference:
Explanation:
Business dependency assessment is a process of determining the dependency of a business on certain
information resources. It is not an outcome or a product of effective security management. Strategic
alignment is an outcome of effective security governance. Where there is good governance, there is likely to be strategic alignment. Risk assessment is not an outcome of effective security governance; it is a
process. Planning comes at the beginning of effective security governance, and is not an outcome but a process.
QUESTION 82
How would an information security manager balance the potentially conflicting requirements of an international organization’s security standards and local regulation?
A. Give organization standards preference over local regulations
B. Follow local regulations only
C. Make the organization aware of those standards where local regulations causes conflicts
D. Negotiate a local version of the organization standards
Correct Answer: D
Explanation
Explanation/Reference:
Explanation:
Adherence to local regulations must always be the priority. Not following local regulations can prove detrimental to the group organization. Following local regulations only is incorrect since there needs to be
some recognition of organization requirements. Making an organization aware of standards is a sensible
step, but is not a total solution. Negotiating a local version of the organization standards is the most
effective compromise in this situation.
QUESTION 83
Who should drive the risk analysis for an organization?
A. Senior management
B. Security manager
C. Quality manager
D. Legal department
300-320 exam Correct Answer: B
Explanation
Explanation/Reference:
Explanation:
Although senior management should support and sponsor a risk analysis, the know-how and the
management of the project will be with the security department. Quality management and the legal department will contribute to the project.
QUESTION 84
The FIRST step in developing an information security management program is to:
A. identify business risks that affect the organization.
B. clarify organizational purpose for creating the program.
C. assign responsibility for the program.
D. assess adequacy of controls to mitigate business risks.
Correct Answer: B
Explanation
Explanation/Reference:
Explanation:
In developing an information security management program, the first step is to clarify the organization’s purpose for creating the program. This is a business decision based more on judgment than on any specific quantitative measures. After clarifying the purpose, the other choices are assigned and acted
upon.
QUESTION 85
Which of the following is the MOST important to keep in mind when assessing the value of information?
A. The potential financial loss
B. The cost of recreating the information
C. The cost of insurance coverage
D. Regulatory requirement
300-320 dumps Correct Answer: A
Explanation
Explanation/Reference:
Explanation:
The potential for financial loss is always a key factor when assessing the value of information. Choices B,
C and D may be contributors, but not the key factor.
QUESTION 86
What would a security manager PRIMARILY utilize when proposing the implementation of a security
solution?
A. Risk assessment report
B. Technical evaluation report
C. Business case
D. Budgetary requirements
Correct Answer: C
Explanation
Explanation/Reference:
Explanation:
The information security manager needs to prioritize the controls based on risk management and the
requirements of the organization. The information security manager must look at the costs of the various
controls and compare them against the benefit the organization will receive from the security solution. The information security manager needs to have knowledge of the development of business cases to illustrate the costs and benefits of the various controls. All other choices are supplemental.
QUESTION 87
To justify its ongoing security budget, which of the following would be of MOST use to the information security’ department?
A. Security breach frequency
B. Annualized loss expectancy (ALE)
C. Cost-benefit analysis
D. Peer group comparison
300-320 pdf Correct Answer: C
Explanation
Explanation/Reference:
Explanation:
Cost-benefit analysis is the legitimate way to justify budget. The frequency of security breaches may assist
the argument for budget but is not the key tool; it does not address the impact. Annualized loss expectancy (ALE) does not address the potential benefit of security investment. Peer group comparison would provide a good estimate for the necessary security budget but it would not take into account the specific needs of the organization.
QUESTION 88
Which of the following situations would MOST inhibit the effective implementation of security governance:
A. The complexity of technology
B. Budgetary constraints
C. Conflicting business priorities
D. High-level sponsorship
Correct Answer: D
Explanation
Explanation/Reference:
Explanation:
The need for senior management involvement and support is a key success factor for the implementation
of appropriate security governance. Complexity of technology, budgetary constraints and conflicting
business priorities are realities that should be factored into the governance model of the organization, and should not be regarded as inhibitors.
QUESTION 89
To achieve effective strategic alignment of security initiatives, it is important that:
A. Steering committee leadership be selected by rotation.
B. Inputs be obtained and consensus achieved between the major organizational units.
C. The business strategy be updated periodically.
D. Procedures and standards be approved by all departmental heads.
300-320 vce Correct Answer: B
Explanation
Explanation/Reference:
Explanation:
It is important to achieve consensus on risks and controls, and obtain inputs from various organizational
entities since security needs to be aligned to the needs of the organization. Rotation of steering committee leadership does not help in achieving strategic alignment. Updating business strategy does not lead to
strategic alignment of security initiatives. Procedures and standards need not be approved by all departmental heads
QUESTION 90
What would be the MOST significant security risks when using wireless local area network (LAN)
technology?
A. Man-in-the-middle attack
B. Spoofing of data packets
C. Rogue access point
D. Session hijacking
Correct Answer: C
Explanation
Explanation/Reference:
Explanation:
A rogue access point masquerades as a legitimate access point The risk is that legitimate users may connect through this access point and have their traffic monitored. All other choices are not dependent on the use of a wireless local area network (LAN) technology.
QUESTION 91
When developing incident response procedures involving servers hosting critical applications, which of the following should be the FIRST to be notified?
A. Business management
B. Operations manager
C. Information security manager
D. System users
300-320 exam Correct Answer: C
Explanation
Explanation/Reference:
Explanation:
The escalation process in critical situations should involve the information security manager as the first
contact so that appropriate escalation steps are invoked as necessary. Choices A, B and D would be
notified accordingly.
QUESTION 92
In implementing information security governance, the information security manager is PRIMARILY
responsible for:
A. developing the security strategy.
B. reviewing the security strategy.
C. communicating the security strategy.
D. approving the security strategy
Correct Answer: A
Explanation
Explanation/Reference:
Explanation:
The information security manager is responsible for developing a security strategy based on business
objectives with the help of business process owners. Reviewing the security strategy is the responsibility of a steering committee. The information security manager is not necessarily responsible for communicating or approving the security strategy.
QUESTION 93
An information security strategy document that includes specific links to an organization’s business
activities is PRIMARILY an indicator of:
A. performance measurement.
B. integration.
C. alignment.
D. value delivery.
300-320 dumps Correct Answer: C
Explanation
Explanation/Reference:
Explanation:
Strategic alignment of security with business objectives is a key indicator of performance measurement. In guiding a security program, a meaningful performance measurement will also rely on an understanding of business objectives, which will be an outcome of alignment. Business linkages do not by themselves indicate integration or value delivery. While alignment is an important precondition, it is not as important an indicator.
QUESTION 94
When an organization is setting up a relationship with a third-party IT service provider, which of the
following is one of the MOST important topics to include in the contract from a security standpoint?
A. Compliance with international security standards.
B. Use of a two-factor authentication system.
C. Existence of an alternate hot site in case of business disruption.
D. Compliance with the organization’s information security requirements.
Correct Answer: D
Explanation
Explanation/Reference:
Explanation:
Prom a security standpoint, compliance with the organization’s information security requirements is one of the most important topics that should be included in the contract with third-party service provider. The scope of implemented controls in any ISO 27001-compliant organization depends on the security requirements established by each organization. Requiring compliance only with this security standard does not guarantee that a service provider complies with the organization’s security requirements. The
requirement to use a specific kind of control methodology is not usually stated in the contract with third
party service providers.
QUESTION 95
To justify the need to invest in a forensic analysis tool, an information security manager should FIRST:
A. review the functionalities and implementation requirements of the solution.
B. review comparison reports of tool implementation in peer companies.
C. provide examples of situations where such a tool would be useful.
D. substantiate the investment in meeting organizational needs.
300-320 pdf Correct Answer: D
Explanation
Explanation/Reference:
Explanation:
Any investment must be reviewed to determine whether it is cost effective and supports the organizational strategy. It is important to review the features and functionalities provided by such a tool, and to provide examples of situations where the tool would be useful, but that comes after substantiating the investment and return on investment to the organization.
QUESTION 96
The MOST useful way to describe the objectives in the information security strategy is through:
A. attributes and characteristics of the ‘desired state.”
B. overall control objectives of the security program.
C. mapping the IT systems to key business processes.
D. calculation of annual loss expectations.
Correct Answer: A
Explanation
Explanation/Reference:
Explanation:
Security strategy will typically cover a wide variety of issues, processes, technologies and outcomes that
can best be described by a set of characteristics and attributes that are desired. Control objectives are
developed after strategy and policy development. Mapping IT systems to key business processes does not
address strategy issues. Calculation of annual loss expectations would not describe the objectives in the
information security strategy.

In this competitive Designing Cisco Network Service Architectures exam environment, everyone is struggling hard to achieve maximum skills and knowledge in Cisco 300-320 dumps practice test to surpass others in qualities and skills. “Designing Cisco Network Service Architectures”, also known as 300-320 exam, is a Cisco certification which covers all the knowledge points of the real Cisco exam. Pass4itsure Cisco 300-320 dumps exam questions answers are updated (503 Q&As) are verified by experts. The associated certifications of 300-320 dumps is CCDP. Our Cisco 300-320 sample questions and ARCH dumps have designed CCDP 300-320 practice test preparation materials in order to solve the problems for https://www.pass4itsure.com/300-320.html dumps ARCH.