High recommend you prepare for CompTIA PenTest+ PT0–001 exam: (1. PT0–001 exam practice test, 2. Pass4itsure CompTIA expert.). Pass4itsure CompTIA PenTest+ PT0–001 practice exams are based on the exam objectives, all the real exam questions are great and answers are accurate. Download the full Pass4itsure PT0–001 dumps https://www.pass4itsure.com/pt0-001.html (Total Questions: 202 Q&A PT0–001 Practice Test).
Update CompTIA PenTest+ PT0–001 exam questions answers
QUESTION 1
A penetration tester has successfully exploited an application vulnerability and wants to remove the command history
from the Linux session. Which of the following will accomplish this successfully?
A. history –remove
B. cat history I clear
C. rm -f ./history
D. history -c
Correct Answer: D
QUESTION 2
A security consultant is trying to attack a device with a previously identified user account.
……
Get complete free CompTIA PT0–001 exam practice questions:https://www.downloadzpdf.com/share-free-comptia-pt0-001-exam-questions-and-comptia-pt0-001-dumps-pdf/
Latest CompTIA PT0–001 actual exam questions for free (update 2021.7)! If you want to read more, this site recommends a complete online blog on CompTIA exam practice questions: downloadzpdf.com. Here, you have everything you need to easily prepare and pass the certification exam.
Share CompTIA PenTest+ PT0–001 practice test for free
QUESTION 1
A client has voiced concern about the number of companies being breached by remote attackers, who are looking for
trade secrets. Which of the following BEST describes the type of adversaries this would identify?
A. Script kiddies
B. APT actors
C. Insider threats
D. Hacktrvist groups
Correct Answer: B
Reference: https://en.wikipedia.org/wiki/Advanced_persistent_threat
QUESTION 2
A company performed an annual penetration test of its environment. In addition to several new findings, all of the
previously identified findings persisted on the latest report. Which of the following is the MOST likely reason?
A. Infrastructure is being replaced with similar hardware and software.
B. Systems administrators are applying the wrong patches.
C. The organization is not taking action to remediate identified findings.
D. The penetration testing tools were misconfigured.
Correct Answer: C
QUESTION 3
A penetration tester was able to enter an SQL injection command into a text box and gain access to the information
store on the database. Which of the following is the BEST recommendation that would mitigate the vulnerability?
A. Randomize the credentials used to log in
B. Install host-based intrusion detection
C. Implement input normalization
D. Perform system hardening
Correct Answer: D
QUESTION 4
A penetration tester has successfully exploited an application vulnerability and wants to remove the command history
from the Linux session. Which of the following will accomplish this successfully?
A. history –remove
B. cat history I clear
C. rm -f ./history
D. history -c
Correct Answer: D
QUESTION 5
If a security consultant comes across a password hash that resembles the following b117 525b3454
7Oc29ca3dBaeOb556ba8 Which of the following formats is the correct hash type?
A. Kerberos
B. NetNTLMvl
C. NTLM
D. SHA-1
Correct Answer: D
QUESTION 6
In which of the following components is an exploited vulnerability MOST likely to affect multiple running application
containers at once?
A. Common libraries
B. Configuration files
C. Sandbox escape
D. ASLR bypass
Correct Answer: A
Reference: https://www.stackrox.com/post/2019/02/the-runc-vulnerability-a-deep-dive-on-protecting-yourself/
QUESTION 7
During post-exploitation, a tester identifies that only system binaries will pass an egress filter and store a file with the
following command:
c: \creditcards.db>c:\winit\system32\calc.exe:creditcards.db
Which of the following file system vulnerabilities does this command take advantage of?
A. Hierarchical file system
B. Alternate data streams
C. Backdoor success
D. Extended file system
Correct Answer: B
QUESTION 8
A penetration tester has been asked to conduct OS fingerprinting with Nmap using a company-provide text file that
contain a list of IP addresses.
Which of the following are needed to conduct this scan? (Select TWO).
A. -O
B. _iL
C. _sV
D. -sS
E. -oN
F. -oX
Correct Answer: AB
Reference https://securitytrails.com/blog/top-15-nmap-commands-to-scan-remote-hosts#six-scan-hosts-and-ipaddresses-reading-from-a-text-file
QUESTION 9
A penetration tester has been assigned to perform an external penetration assessment of a company. Which of the
following steps would BEST help with the passive-information-gathering process? (Choose two.)
A. Wait outside of the company\\’s building and attempt to tailgate behind an employee.
B. Perform a vulnerability scan against the company\\’s external netblock, identify exploitable vulnerabilities, and attempt
to gain access.
C. Use domain and IP registry websites to identify the company\\’s external netblocks and external facing applications.
D. Search social media for information technology employees who post information about the technologies they work
with.
E. Identify the company\\’s external facing webmail application, enumerate user accounts and attempt password
guessing to gain access.
Correct Answer: DE
QUESTION 10
A penetration tester observes that the content security policy header is missing during a web application penetration
test. Which of the following techniques would the penetration tester MOST likely perform?
A. Command injection attack
B. Clickjacking attack
C. Directory traversal attack
D. Remote file inclusion attack
Correct Answer: B
References: https://geekflare.com/http-header-implementation/
QUESTION 11
The following command is run on a Linux file system:
Chmod 4111 /usr/bin/sudo
Which of the following issues may be exploited now?
A. Kernel vulnerabilities
B. Sticky bits
C. Unquoted service path
D. Misconfigured sudo
Correct Answer: B
QUESTION 12
Which of the following BEST describes some significant security weaknesses with an ICS, such as those used in
electrical utility facilities, natural gas facilities, dams, and nuclear facilities?
A. ICS vendors are slow to implement adequate security controls.
B. ICS staff are not adequately trained to perform basic duties.
C. There is a scarcity of replacement equipment for critical devices.
D. There is a lack of compliance for ICS facilities.
Correct Answer: B
QUESTION 13
Click the exhibit button.
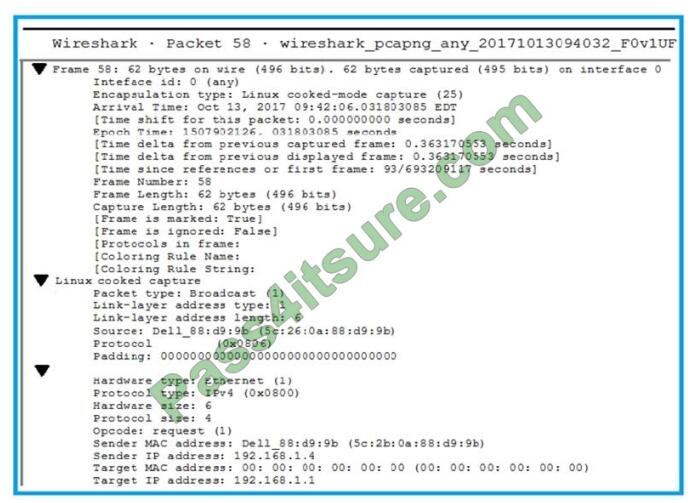
A penetration tester is performing an assessment when the network administrator shows the tester a packet sample that
is causing trouble on the network. Which of the following types of attacks should the tester stop?
A. SNMP brute forcing
B. ARP spoofing
C. DNS cache poisoning
D. SMTP relay
Correct Answer: A
Latest reviews of Pass4itsure PT0–001 practice exam
Just passed with this dumps. This is just enough for passing the exam.
Just took the exam today and passed! This dump is about 97% valid for me. Like everyone says there are a couple of new questions that are not on this dumps. I suggest studying other resources and dumps to fill in the gap. I suggest really knowing why the answers are correct instead of just memorizing the answers.
I have passed my exam today..thanks
I have passed the exam 4 days ago. No new questions. Answers are all correct.
Latest Pass4itsure CompTIA exam discount code 2021
Pass4itsure shares the latest CompTIA exam Discount code “CompTIA“.

Study tips help your final CompTIA PT0-001 exam

Free CompTIA PenTest+ PT0–001 pdf dumps download
[Latest PDF] CompTIA PenTest+ PT0–001 pdf dumps from Google Drive: https://drive.google.com/file/d/1v1UxF3DIRvENe37PiDMsCveBxAgVF22f/view?usp=sharing
Summarize:
Here you will get everything, which you are looking for. The latest CompTIA PT0–001 practice test questions can help you pass the exam! Visit here:https://www.pass4itsure.com/pt0-001.html CompTIA PT0–001 dumps!
Good Luck !!!
