
Pass4itSure CS0-002 exam dumps is an effective CompTIA Cybersecurity Analyst (CySA+) exam preparation that updates the CS0-002 exam preparation material with a unique 908 questions to help you easily pass the CS0-002 exam.
Before planning the CompTIA CySA+ CS0-002 exam is, you can select the latest Pass4itSure CS0-002 exam dumps https://www.pass4itsure.com/cs0-002.html as exam preparation.
Will you summarize the CompTIA Cybersecurity Analyst (CySA+) exam in a nutshell?
CompTIA CySA+ CS0-002 is an intermediate high-risk cybersecurity analyst certification that includes both practice-based and multiple-choice questions.
There are up to 85 questions in the real exam that you need to answer in 165 minutes and score 750 or higher to pass. It costs $392 to take the exam.
Note:
The new CompTIA CySA+ (CS0-003) exam will be held in spring 2023!
Is CompTIA CySA+ CS0-002 really hard to pass?
Not difficult. Just master the preparation CS0-002 exam method effectively.
Use the latest CS0-002 exam dumps – Pass4itSure CS0-002 exam dumps.
With it, plus regular practice, it’s easy to pass the CompTIA Cybersecurity Analyst (CySA+) exam.
What are the Pass4itSure CS0-002 exam dumps preparation materials?
Pass4itSure will provide you with two forms of materials for you to prepare:
- CS0-002 PDF
- CS0-002 VCE
All contain the latest 908 exam practice questions and explanations to help you prepare for the exam clearly.
Where can I get free CS0-002 exam dumps preparation materials?
Here.
Free CS0-002 exam dumps PDF – Updated study material: https://drive.google.com/file/d/1CqJBDgk8Xt-uhgrnOnP-HZLuwHIlZFNh/view?usp=sharing
[Updated 2022.9] Free CompTIA CS0-002 Exam Questions
QUESTION 1
A cybersecurity analyst was asked to discover the hardware address of 30 networked assets. From a command line,
which of the following tools would be used to provide ARP scanning and reflects the MOST efficient method for
accomplishing the task?
A. nmap
B. tracert
C. ping -a
D. nslookup
Correct Answer: A
QUESTION 2
During which of the following NIST risk management framework steps would an information system security engineer
identify inherited security controls and tailor those controls to the system?
A. Categorize
B. Select
C. Implement
D. Assess
Correct Answer: B
QUESTION 3
After completing a vulnerability scan, the following output was noted:
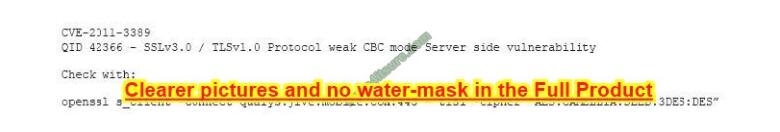
Which of the following vulnerabilities has been identified?
A. PKI transfer vulnerability.
B. Active Directory encryption vulnerability.
C. Web application cryptography vulnerability.
D. VPN tunnel vulnerability.
Correct Answer: C
QUESTION 4
HOTSPOT
Welcome to the Enterprise Help Desk System. Please work the ticket escalated to you in the help desk ticket queue.
INSTRUCTIONS Click on the ticket to see the ticket details. Additional content is available on tabs within the ticket.
First, select the appropriate issue from the drop-down menu. Then, select the MOST likely root cause from second dropdown menu. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
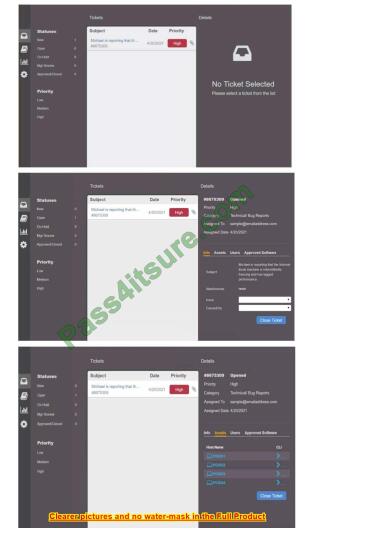
Hot Area:
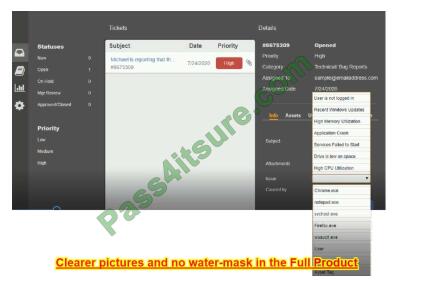
Correct Answer:
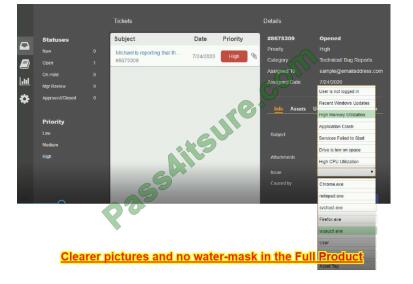
QUESTION 5
A vulnerability scan has returned the following information:
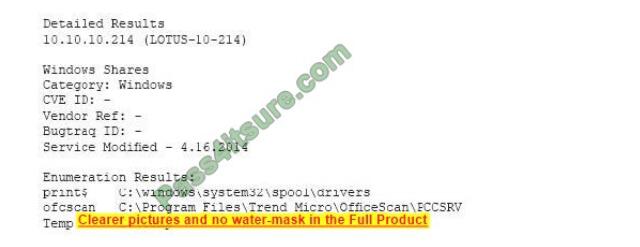
Which of the following describes the meaning of these results?
A. There is an unknown bug in a Lotus server with no Bugtraq ID.
B. Connecting to the host using a null session allows enumeration of share names.
C. Trend Micro has a known exploit that must be resolved or patched.
D. No CVE is present, so it is a false positive caused by Lotus running on a Windows server.
Correct Answer: B
QUESTION 6
A security analyst is preparing for the company\’s upcoming audit. Upon review of the company\’s latest vulnerability
scan, the security analyst finds the following open issues:

Which of the following vulnerabilities should be prioritized for remediation FIRST?
A. ICMP timestamp request remote date disclosure
B. Anonymous FTP enabled
C. Unsupported web server detection
D. Microsoft Windows SMB service enumeration via \srvsvc
Correct Answer: C
QUESTION 7
An employee in the billing department accidentally sent a spreadsheet containing payment card data to a recipient
outside the organization The employee intended to send the spreadsheet to an internal staff member with a similar
name and was unaware of the mistake until the recipient replied to the message In addition to retraining the employee,
which of the following would prevent this from happening in the future?
A. Implement outgoing filter rules to quarantine messages that contain card data
B. Configure the outgoing mail filter to allow attachments only to addresses on the whitelist
C. Remove all external recipients from the employee\’s address book
D. Set the outgoing mail filter to strip spreadsheet attachments from all messages.
Correct Answer: B
QUESTION 8
A cybersecurity analyst is completing an organization\’s vulnerability report and wants it to reflect assets accurately.
Which of the following items should be in the report?
A. Processor utilization
B. Virtual hosts
C. Organizational governance
D. Log disposition
E. Asset isolation
Correct Answer: B
QUESTION 9
An organization has several system that require specific logons Over the past few months, the security analyst has
noticed numerous failed logon attempts followed by password resets. Which of the following should the analyst do to
reduce the occurrence of legitimate failed logons and password resets?
A. Use SSO across all applications
B. Perform a manual privilege review
C. Adjust the current monitoring and logging rules
D. Implement multifactor authentication
Correct Answer: A
QUESTION 10
A security analyst is reviewing output from a CVE-based vulnerability scanner. Before conducting the scan, the analyst
was careful to select only Windows-based servers in a specific datacenter. The scan revealed that the datacenter
includes 27 machines running Windows 2003 Server Edition (Win2003SE). In 2015, there were 36 new vulnerabilities
discovered in the Win2003SE environment. Which of the following statements are MOST likely applicable? (Choose
two.)
A. Remediation is likely to require some form of compensating control.
B. Microsoft\’s published schedule for updates and patches for Win2003SE have continued uninterrupted.
C. Third-party vendors have addressed all of the necessary updates and patches required by Win2003SE.
D. The resulting report on the vulnerability scan should include some reference that the scan of the datacenter included
27 Win2003SE machines that should be scheduled for replacement and deactivation.
E. Remediation of all Win2003SE machines requires changes to configuration settings and compensating controls to be
made through Microsoft Security Center\’s Win2003SE Advanced Configuration Toolkit.
Correct Answer: DE
QUESTION 11
A security analyst has performed various scans and found vulnerabilities in several applications that affect production
data. Remediation of all exploits may cause certain applications to no longer work. Which of the following activities
would need to be conducted BEFORE remediation?
A. Fuzzing
B. Input validation
C. Change control
D. Sandboxing
Correct Answer: C
QUESTION 12
In reviewing firewall logs, a security analyst has discovered the following IP address, which several employees are using
frequently: The organization\’s servers use IP addresses in the 192.168.0.1/24 CIDR. Additionally, the analyst has noticed that
corporate data is being stored at this new location. A few of these employees are on the management and executive
management teams. The analyst has also discovered that there is no record of this IP address or service in reviewing
the known locations of managing system assets. Which of the following is occurring in this scenario?
A. Malicious process
B. Unauthorized change
C. Data exfiltration
D. Unauthorized access
Correct Answer: C
QUESTION 13
SIMULATION
Approximately 100 employees at your company have received a phishing email. As a security analyst you have been
tasked with handling this situation.
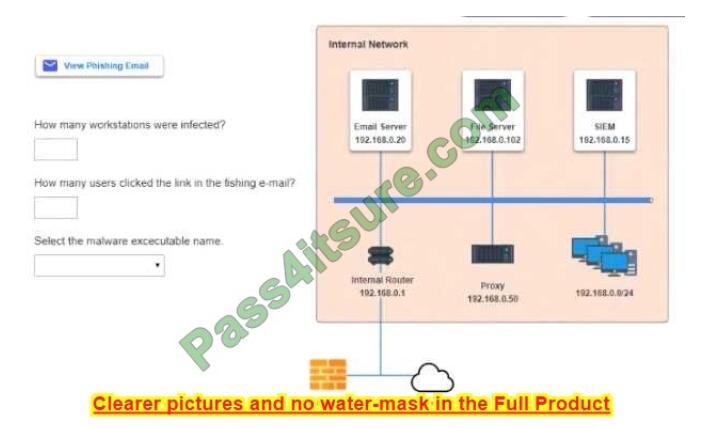
A. Check the below.
B. PlaceHolder
C. PlaceHolder
D. PlaceHolder
Correct Answer: A
Select the following answer as per diagram below:
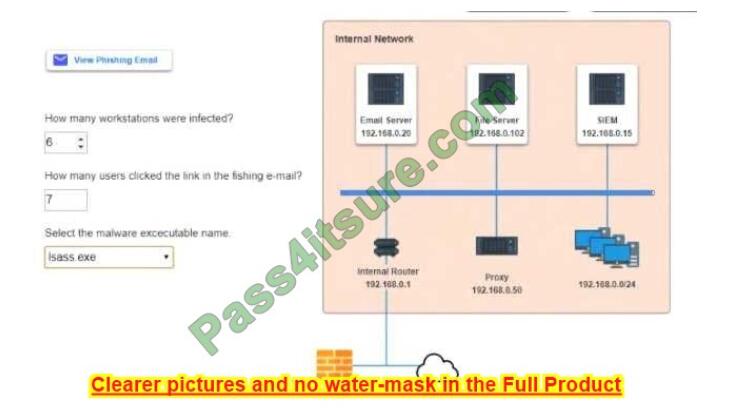
……
Use the latest CS0-002 exam dumps https://www.pass4itsure.com/cs0-002.html to happily prepare for the CompTIA Cybersecurity Analyst (CySA+) exam.
Ducktown.org provides a wealth of exam practice materials designed to pass the exam. Learn more and explore all CompTIA Series exam questions.